What Is a VPN Tunnel?
A VPN tunnel is a secure, encrypted connection between a network device and a VPN server that safeguards data transfer over the internet.
The VPN tunnel creates a private pathway, shielding transmitted information from interception and unauthorized access. Encryption algorithms convert data into unreadable code during transit, ensuring that even if data is intercepted, it remains inaccessible and secure.
How Does VPN Tunneling Work?
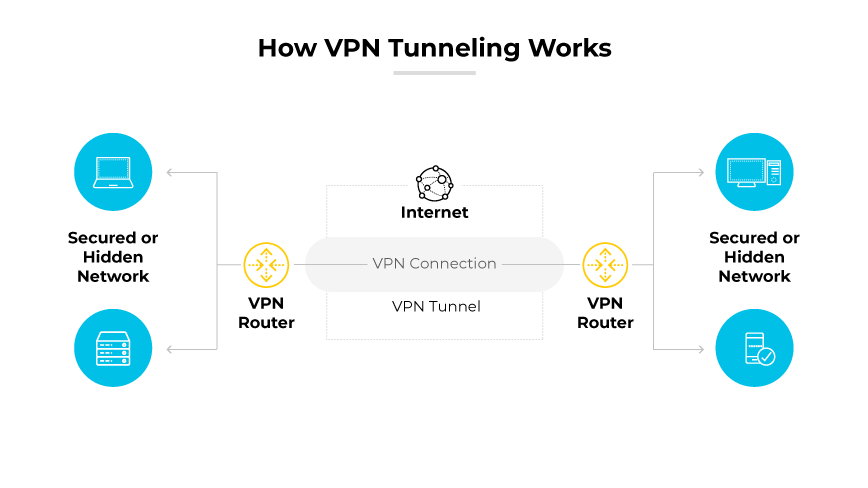
VPN tunneling involves the creation of a secure and encrypted connection over a network, typically the internet. This connection is referred to as a "tunnel" because it provides a safe passageway for data to travel between a device and a VPN server.
VPN tunneling conceals a user's IP address and encrypts their data. This offers protection, especially when using unsecured public Wi-Fi. The encryption process can be compared to sending a sealed envelope through the mail. Even if postal workers see or handle the envelope, the contents remain private unless someone opens it.
VPN tunneling includes safeguards such as a kill switch, which halts internet traffic if the VPN connection drops. This prevents the user's public IP address from becoming visible, which maintains the integrity of the secure tunnel.
The tunneling process involves several steps to ensure security and privacy:
1. Initiation of the VPN connection
A user must select a VPN service and connect their device to the chosen VPN server.
2. Establishment of an encrypted tunnel
The VPN application on the user's device generates an encrypted channel. This encryption shields the internet traffic from unauthorized access as it moves through the user's internet connection to the VPN server.
3. Encryption of data
The data transmitted through the tunnel is encrypted using a specific protocol, transforming the information into a coded format known as "ciphertext." This encrypted data is undecipherable to anyone without the proper decryption keys.
4. Decryption at the VPN server
The VPN server receives the encrypted data and uses keys to decrypt it. Once decrypted, the data can continue to its intended destination on the internet.
5. Return of data to the user's device
Data sent from the internet back to the user also passes through the encrypted tunnel, ensuring privacy and security in both directions.
Types of VPN Tunneling Protocols
Point-to-Point Tunneling Protocol (PPTP)
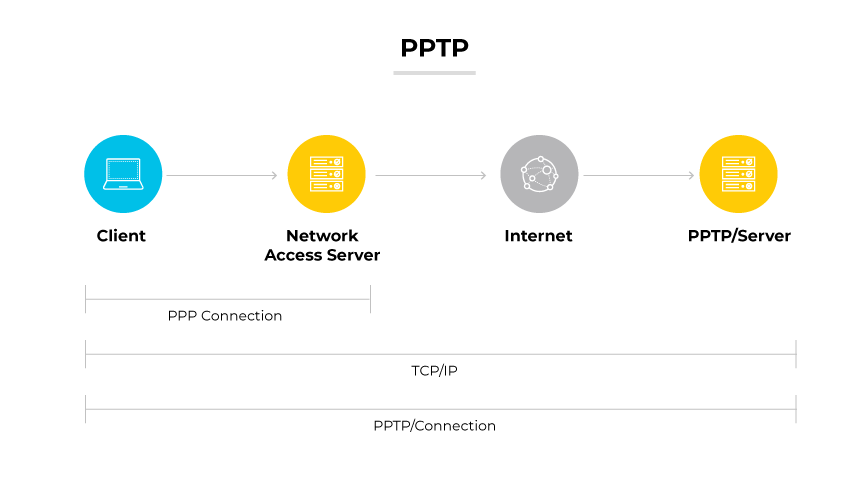
PPTP facilitates the creation of a private network across the internet, enabling secure data transfer. This protocol encapsulates data packets. Ease of setup is a key advantage, requiring minimal configuration. The encryption PPTP offers is not as strong as newer protocols, making it susceptible to security breaches.
Layer 2 Tunneling Protocol (L2TP)/IPSec
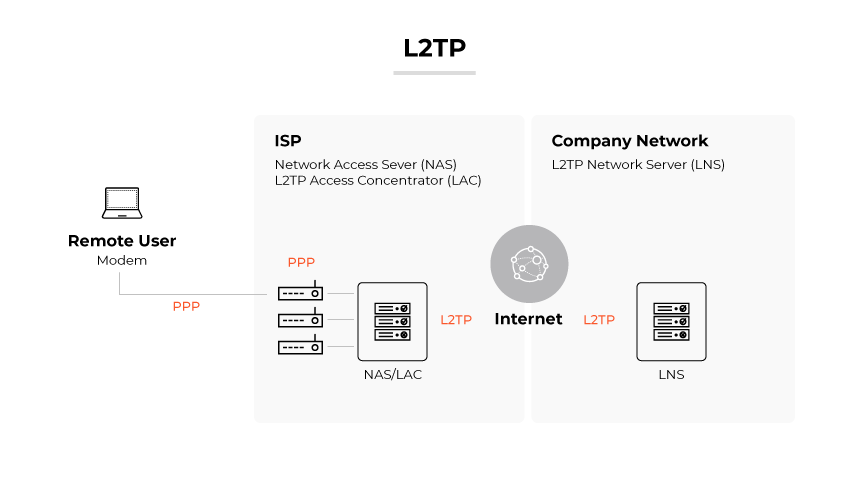
L2TP/IPSec is a combination of two protocols: L2TP to create the tunnel and IPSec for data encryption and secure communications.
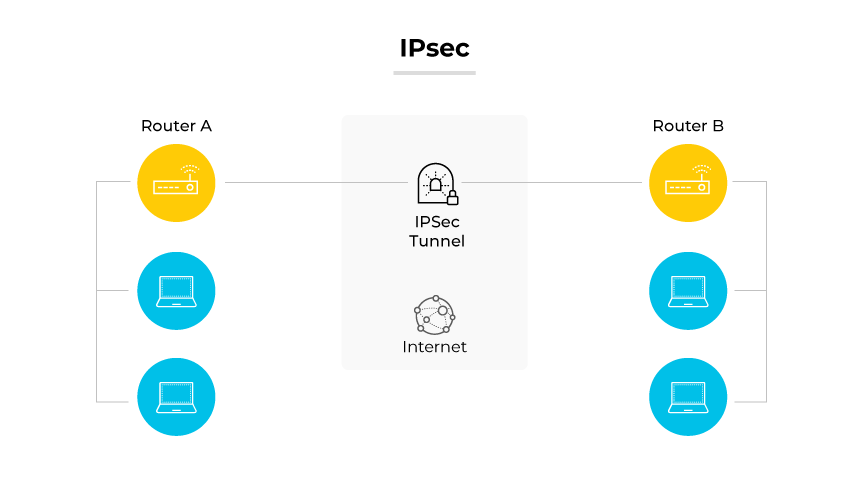
This protocol is recognized for its compatibility with a wide array of devices and operating systems. However, the dual layers of security can potentially slow down transmission speed. Also, its use of fixed ports can result in complications with some firewalls.
Secure Socket Tunneling Protocol (SSTP)
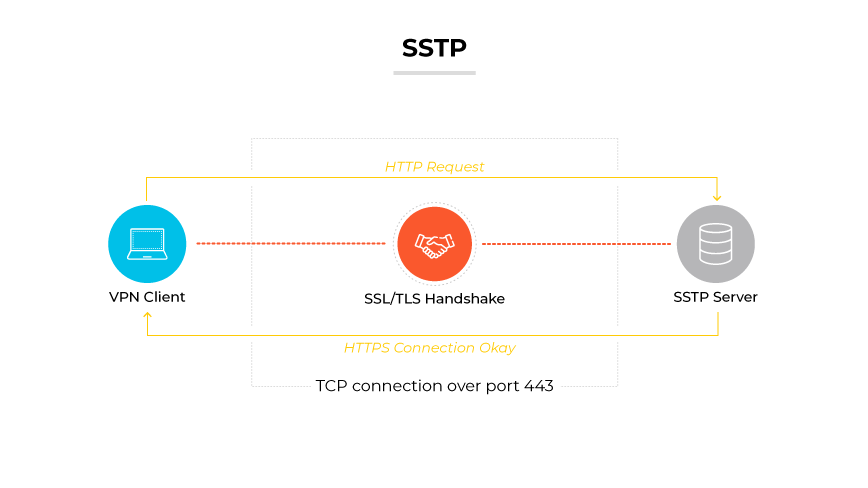
SSTP utilizes SSL 3.0 for secure data passage through the tunnel. It is known for robust encryption capabilities. SSTP does not depend on fixed ports. Consequently, one of its distinctive benefits is the ability to bypass firewalls. The protocol's limitation lies in its platform exclusivity, as it does not support non-Windows systems.
OpenVPN
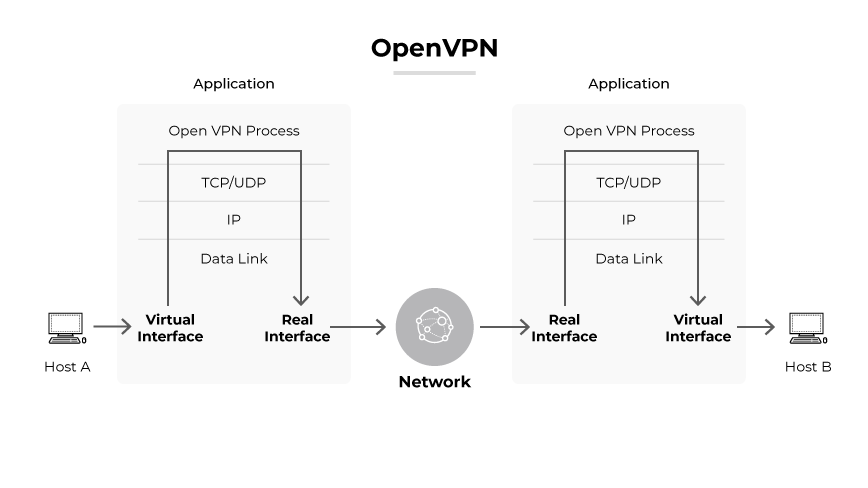
OpenVPN, an open-source protocol, offers strong encryption and the ability to work across multiple operating systems. It is highly regarded for flexibility and security strength, employing AES 256-bit encryption. While OpenVPN allows for significant customization, it requires more complex setup procedures, which can be mitigated by using configuration software.
Internet Key Exchange version 2 (IKEv2)/IPSec
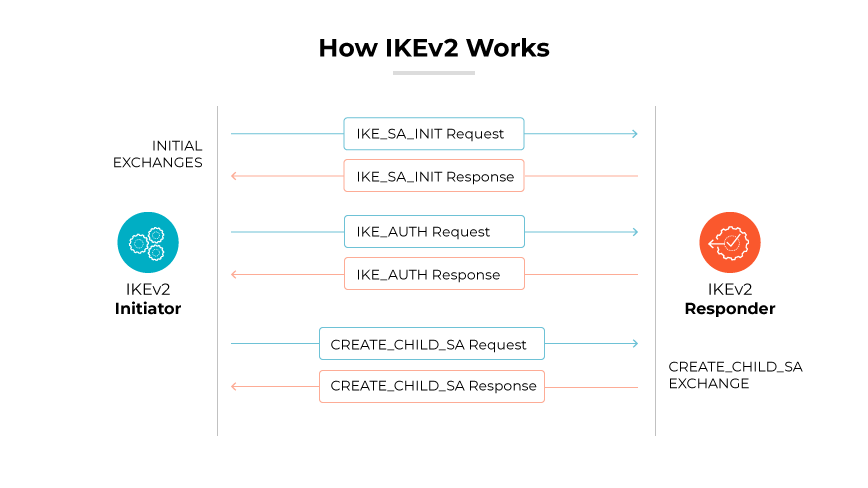
IKEv2, in combination with IPSec, delivers a secure, efficient VPN experience. It is recognized for its ability to re-establish a VPN connection swiftly when switching networks, making it a suitable choice for mobile devices. Native support on certain platforms, like iOS, adds to its appeal, though the setup can be intricate on non-native platforms.
WireGuard
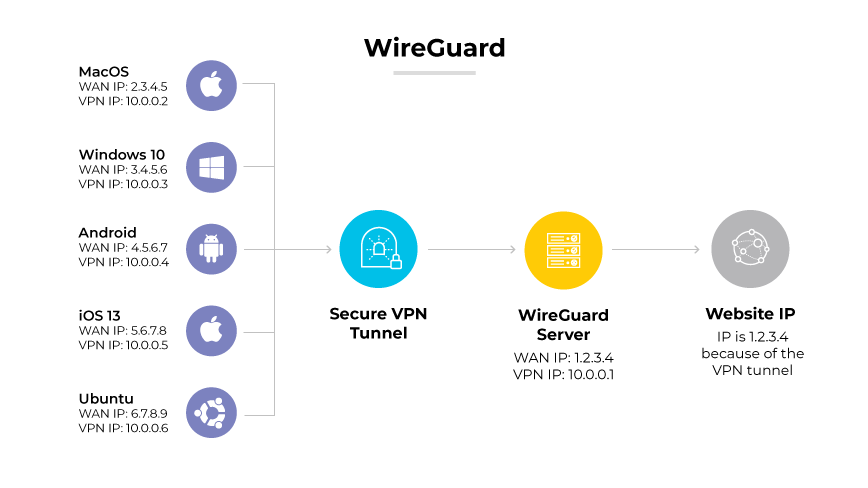
WireGuard is a modern VPN protocol praised for its minimalistic design and high performance. With state-of-the-art encryption, it is both secure and fast. WireGuard's lightweight nature makes it easy to implement and audit, contributing to its growing popularity, especially in mobile applications.
What Is VPN Split Tunneling?

VPN split tunneling is a feature that allows a user to route some internet traffic through a secure VPN, while other traffic accesses the internet directly, bypassing the VPN. This method permits the division of network traffic into two streams. One stream is encrypted and routed through a VPN tunnel, and the other connects to the internet. This is particularly useful when simultaneous access to resources in both private and public networks is required.
The advantage of split tunneling is its efficiency. By only directing necessary traffic through the VPN, it can conserve bandwidth and improve speed for the activities that do not require encryption. For instance, an employee could access their company’s internal documents through the VPN while streaming music directly via their local internet connection, which does not require VPN security.
However, there are potential risks. The traffic that does not use the VPN is unencrypted, making it potentially vulnerable to threats like data interception. While split tunneling can optimize network performance, it must be implemented judiciously to maintain security where it is most needed. This function is contingent on the VPN service provider's support and may vary across different devices and operating systems.
