- What is Security Analytics?
-
What is SIEM?
- SIEM: The Foundation for XSIAM
- How SIEM Works
- Key Functions and Benefits of SIEM
- Role of AI and ML in SIEM
- SIEM Integration
- SIEM Use Cases
- How to Choose a SIEM Solution
- Best Practices for SIEM Implementation
- SIEM vs Other Security Solutions
- What is Cloud SIEM?
- The Evolution of SIEM
- The Future of SIEM
- SIEM FAQs
- What is Security Information and Event Management (SIEM) Integration?
- What is SIEM Logging?
- What Is Security Event Management (SEM)?
- What is a SIEM Solution in a SOC?
- How Do SIEM Tools Benefit SOC Teams?
-
What Is the Role of AI and ML in Modern SIEM Solutions?
- The Evolution of SIEM Systems
- Benefits of Leveraging AI and ML in SIEM Systems
- SIEM Features and Functionality that Leverage AI and ML
- AI Techniques and ML Algorithms that Support Next-Gen SIEM Solutions
- Predictions for Future Uses of AI and ML in SIEM Solutions
- Role of AI and Machine Learning in SIEM FAQs
- What Is Security Information Event Management (SIEM) Software?
- What are SIEM Use Cases?
- What Are Security Information and Event Management (SIEM) Tools?
What is Cloud SIEM?
Cloud SIEM (Security Information and Event Management), also called SIEM-as-a-Service or SIEM SaaS, is a solution that provides visibility into workloads across distributed environments and enables real-time monitoring, analysis, and anomaly alerting to identify threats and speed up incident response.
A cloud SIEM solution can monitor log data from multiple sources, such as endpoint devices and networks, through a unified, cloud-based dashboard. Cloud SIEM solutions offer several cybersecurity benefits over traditional SIEM tools when managing threat detection and gathering threat intelligence across disparate environments.
Why Use a Cloud SIEM?
Cloud SIEM assists in-house security teams in automating the collection, monitoring, and analysis of data from any location. It helps security teams defend against cyberattacks, including known threats identified in the MITRE ATT&CK framework.
This capability is crucial now that most organizations have workforces and critical workloads outside traditional on-premise boundaries. Cloud SIEM also supports integrations with other security operations tools, allowing them to ingest more data for broader observability. The inherent scalability of cloud SIEM allows these systems to gather and correlate massive amounts of data to identify potential security incidents.
Additional Cloud SIEM benefits include the following:
- Elasticity: Cloud SIEM solutions allow organizations to adjust capacity dynamically rather than estimate future resource needs, often resulting in a shortage or surplus.
- Less Expertise and Staff Required: Cloud-based SIEM solutions are designed to be easy to implement, use, and maintain, reducing the level of expertise and the number of staff needed to support them.
- Cost-Effectiveness: Cloud SIEM eliminates the need for complex, resource-intensive, and costly maintenance, avoiding capital expenditures associated with on-premise SIEM deployments.
- Rapid Deployment: Security teams can customize and deploy cloud SIEM solutions faster than traditional on-premise systems.
- Resilience: Cloud SIEM operates in managed environments with automatic backup and recovery functions and is often deployed across multiple locations for redundancy.
- Unified System with All Security and Event Log Data: Security teams can monitor all physical and virtual systems from a unified system, enabling real-time alerts, detection rule updates, risk assessments, and compliance audit reports.
How SIEM Interacts with Cloud Environments and SaaS Applications
SIEM systems enhance security in cloud environments and SaaS applications by collecting and normalizing logs through API integrations with cloud service providers and SaaS platforms. They use advanced analytics and threat intelligence to detect anomalies and potential threats while correlating events across diverse sources.
Automated incident responses and integrations with SOAR platforms enable rapid threat mitigation. SIEMs also provide detailed reporting and audit trails to ensure compliance with regulatory requirements, offering a unified view of security across an organization's entire IT landscape.
Core Cloud SIEM Features and Capabilities
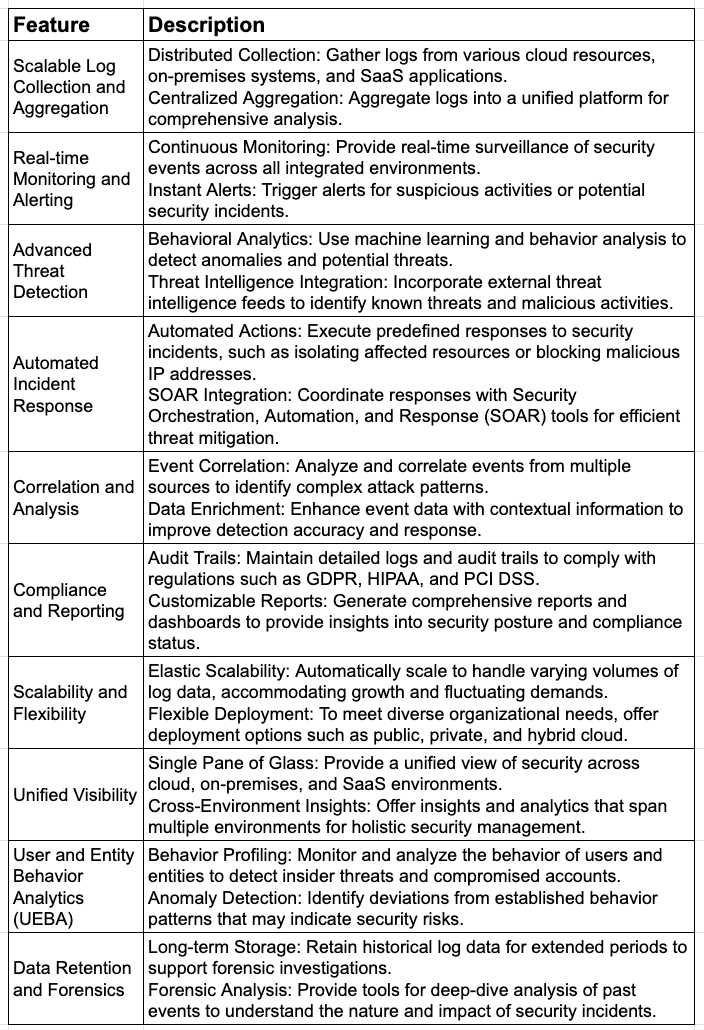
Cloud SIEM Deployment Models
Several models are available for deploying cloud SIEM, with the optimal choice depending on security teams' capabilities, demands, resources, and preferences for responsibility, capital expenditure, and data control. Review the following options to gauge the best fit.
Customer-Deployed Cloud SIEM Model
The customer-deployed model, which falls under the category of infrastructure-as-a-service, is often used as an interim step before embracing a fully cloud-based solution. It is used by organizations that want a high degree of data control and have the resources to cover the cost and responsibility for the infrastructure beyond virtualization.
Cloud-Hosted SIEM Model
This single-tenant model requires less capital expenditure and support from the security team. The vendor provides and manages the hardware and software via the cloud, offering much of the control and security of a customer-deployed solution but at a relatively high cost due to the lack of economies of scale.
Cloud Native SIEM Model
A multi-tenant model offering a complete SaaS solution. This model delivers all the benefits of a cloud SIEM implementation, with vendors providing all hardware, software, and supporting architectures. Organizations have their own dashboards and user interfaces, but backend components are shared, keeping costs lower. Cloud-native SIEM providers build in core functionality with key tools that are pre-configured out of the box.
Cloud SIEM as Managed Service
Cloud SIEM is also a full-service solution, with managed service providers handling all aspects of running the system. This model eliminates the need for organizations to self-operate a security operations center (SOC), with security operations processes managed remotely or in-house.
On-Premise vs. Cloud SIEM Deployment
Like all technology, the right deployment model is dictated by the organization’s security operations requirements, budget, and the security team's capacity and skills.
Characteristics of Organizations that Choose an On-Premise SIEM
- The organization needs a high degree of autonomy, control, and flexibility in its cybersecurity posture.
- Prioritize data privacy to meet strict compliance and legal requirements
- Want the ability to customize and finely tune their SIEM
Characteristics of Organizations that Choose a Cloud SIEM
- Rely heavily on cloud-based operations
- Want the ability to integrate with other cloud systems seamlessly
- Need a high degree of scalability and accessibility
- Seek the deployment and management simplicity of a cloud SIEM
Key Steps for Implementing Cloud SIEM
Successful deployment of Cloud SIEM requires careful planning and execution. Key steps must be taken to implement Cloud SIEM, ensuring your organization can effectively harness its capabilities while addressing potential challenges. These steps establish a powerful, scalable, and efficient Cloud SIEM solution tailored to your security needs.
#1: Understand the Current Environment
Start by gathering information about all digital assets (cloud and on-prem), the current security analytics coverage, and the available technical resources (i.e., systems and people) to support the project. Assess the staff’s skills relative to the requirements for the cloud SIEM deployment and ongoing management, as well as the technical resources, such as bandwidth.
#2: Determine and Prioritize Use Cases
Identify current use cases covered by the legacy SIEM or other security tools. Then, additional use cases should be considered.
#3: Assess Cloud SIEM Solutions
Consider the available cloud SIEM solutions and deployment models. Map each solution’s functionality to the organization's specific requirements and capabilities. Pay attention to how the cloud SIEM aligns with compliance requirements.
#4: Define Goals
Define metrics to quantify the results of the specific objectives for each implementation stage. This is critical for keeping the implementation on schedule, identifying issues, and optimizing systems and processes.
#5: Establish Operational Processes and Roles
Before beginning a cloud SIEM deployment, processes and roles should be determined. This should include the functions to support the implementation and the ongoing support roles and processes needed to manage and maintain the cloud SIEM solution. Policies and detection rules should be updated and created during this step.
#6: Train the Team
Schedule formal training for the security team using the cloud SIEM. Provide training in various formats to make it engaging and optimally reach each constituent. This can include hands-on lab work, reading materials, videos, and ask-the-expert sessions.
#7: Deploy and test the cloud SIEM
The specific steps for deployment will vary based on the model selected, but the process should be articulated and communicated to the security team before it begins. Once the system is live, key use cases should be tested to proactively identify bugs and ensure optimal performance.
Testing frameworks should cover the validation of key functionality and the efficacy and accuracy of threat detection, alert generation, and contextualization of alerts to expedite incident response.
#8: Create Processes for Reviews and Updates
Post-implementation, regular reviews of performance metrics and operational functions should be conducted to keep policies and rules updated and optimized. Performance should also be closely monitored, as this can degrade as data volumes grow over time. In addition, new or improved third-party threat intelligence should be used to improve the detection of security incidents.
Cloud SIEM Challenges
While Cloud SIEM offers numerous advantages, such as scalability and real-time threat detection, organizations might encounter a few challenges. However, proper planning and the right strategies can effectively manage these challenges.
Data Security Concerns
Organizations might worry about the security of sensitive data in the cloud. To address this, reputable Cloud SIEM providers implement robust encryption protocols and comply with stringent security standards to protect data.
Complexity of Integration
Integrating Cloud SIEM with existing systems can be complex. Choosing a solution with comprehensive support and clear integration guidelines can simplify this process and ensure seamless deployment.
Evolving Threat Landscape
The ever-evolving threat landscape can pose challenges for Cloud SIEM solutions. However, leveraging machine learning and regular updates from threat intelligence feeds can keep the system ahead of emerging threats.
Cost Management
Some organizations may be concerned about initial deployment costs. Opting for a scalable, pay-as-you-go model helps manage costs effectively, ensuring that you only pay for the resources you use.
Despite potential challenges, the continuous advancements in Cloud SIEM technology and adherence to industry best practices significantly mitigate these issues. While there are some initial hurdles, the long-term benefits of Cloud SIEM far outweigh these challenges. Organizations that adopt Cloud SIEM can enjoy enhanced security visibility, improved incident response times, and better compliance posture, ultimately leading to a more secure and resilient IT environment.
Considerations of a Cloud Native SIEM Solution
When implementing a cloud-native SIEM, consider these factors for success:
- Bandwidth: Ensure your organization has enough bandwidth to handle the volume of logs and interfaces.
- Cost: Understand initial pricing and future costs as data volume grows.
- Data control: Assess the level of control over your data based on the deployment model.
- Network reliability: Ensure stable and reliable network connectivity between data sources and the cloud SIEM.
- Regulatory and legal compliance: Comply with various regulations and laws concerning sensitive data, including data sovereignty, protection, and privacy rules.
Cloud SIEM FAQs
CISOs and security teams are replacing traditional and cloud SIEM systems with extended security intelligence and automation management (XSIAM). This approach unifies and automates SIEM functionality and other SOC capabilities, allowing analysts to focus on tasks that require human intelligence.
Key integrated functionalities delivered through XSIAM include traditional SIEM and cloud SIEM capabilities, extended detection and response (XDR), endpoint protection, identity threat detection and response (ITDR), attack surface management (ASM), security orchestration, automation, and response (SOAR), cloud detection and response (CDR), and compliance management and reporting support.